Privacy-i EDR
Next-generation antivirus and single-agent solution.
Privacy-i EDR is a ‘Next-Generation Antivirus Solution’ that detects security threats that
bypass typical endpoint security solutions
and responds to attacks in real time.
A single agent that prevents both personal information
leakage and malware infiltration simultaneously.
Resolves the limitations of traditional EDR solutions
by providing an automated solution optimized for proactive threat blocking.

<VB100> certified from <Virus Bulletin>
Somansa Privacy-i EDR achieved the highest A+ rating from Virus Bulletin,
demonstrating a 0% false positive rate and a 99.52% detection rate.
| Results of VB100 Testing | |
|---|---|
| On 100 Thousand Malicious Samples | Result(%) |
| False Positive Rate | 0% |
| Detection Rate (on 100K samples) | 99.52% |
Member of Microsoft Virus Initiative by Microsoft
Receives threat information directly from Microsoft and leverages new native APIs,
to ensure the sustainability of the endpoint security solution.

Pattern & Behavior Detection Engines,
Two-Level Analysis for Advanced Threat Detection
A pattern-based engine is used for initial filtering, followed by an action-based engine for secondary blocking.

Blocks Signature based malware/ransomware

Threats are detected, responded to, and blocked according to their severity level.
Specialized in detecting and preventing new, modified, and fileless attacks.
Optimized for blocking ransomware, newly modified malware, and fileless attacks,
as well as responding to zero-day attacks.
Cyber Attack Kill Chain Analysis Report
MITRE ATT&CK framework has been applied.
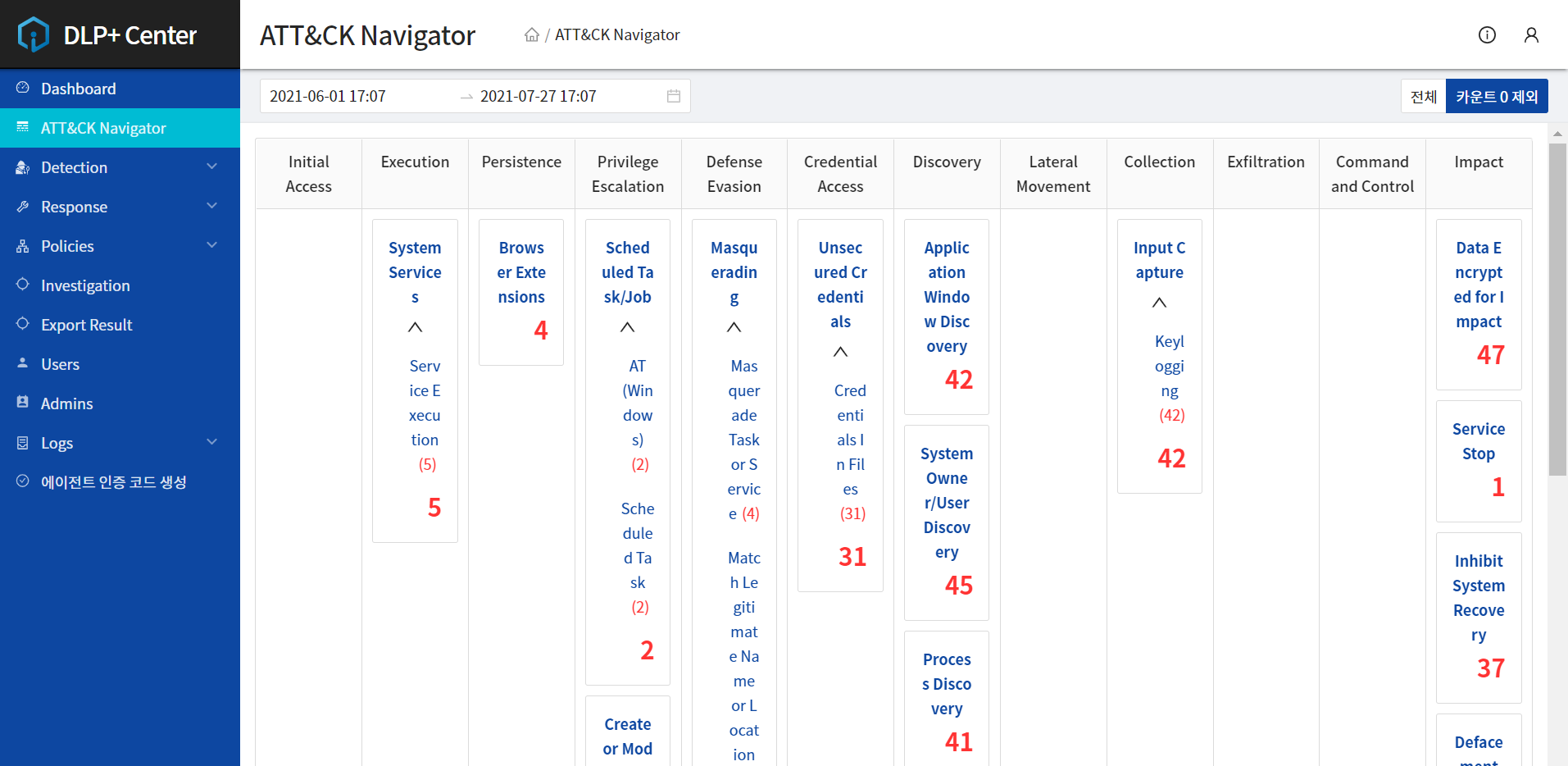
Performs automated endpoint correlation analysis across millions of devices.
Automates malware analysis, detection, and response.
Automated analysis of endpoint correlations across millions of devices Automate malware analysis, detection, and respond
Security companies respond to security threats based on these tactics
The MITRE ATT&CK framework has redefined malicious activities that were previously classified as potentially harmful,
now enabling clear detection and blocking.
Comprehensive Endpoint Security with a Unified Agent
With an agent update, companies using Privacy-i can implement EDR and endpoint security solutions seamlessly.

Personal data security
Personal/confidential Information
and sensitive data

DLP
Personal/confidential information
leakage prevention and control
PC Keeper
PC vulnerability check and analysis

Action-based malicious code
detection and response
Pattern based
antivirus detection and block
Through a single agent, it surpasses the malware blocking and endpoint threat detection of typical EDR solutions, enabling personal data protection, data leakage prevention, and vulnerability scanning.
Proactive Blocking & Response: Automation
Using a detection engine and deep learning, threats are automatically mitigated without requiring administrator intervention.
Ransomware activity is saved and shared with other agents and threat intelligence (TI) systems.
When new threat is detected, will be updated in real-time through TI, protecting data by reducing the spread
Real-time quarantine and backup recovery
Real-time quarantine: Detects and quarantines malware even if a shortcut file is stored on the PC
Real-time backup recovery: Quickly detects anomalous behavior and restores data to just before file tampering.
Simultaneous response on NDR and EDR
Malicious code or ransomware that enters through the network will be blocked in real-time by the DB infrastructure.
Acquired an XDR roadmap that provides quantitative defense across networks and endpoints.
LG Chooses Privacy-i EDR over Crowdstrike
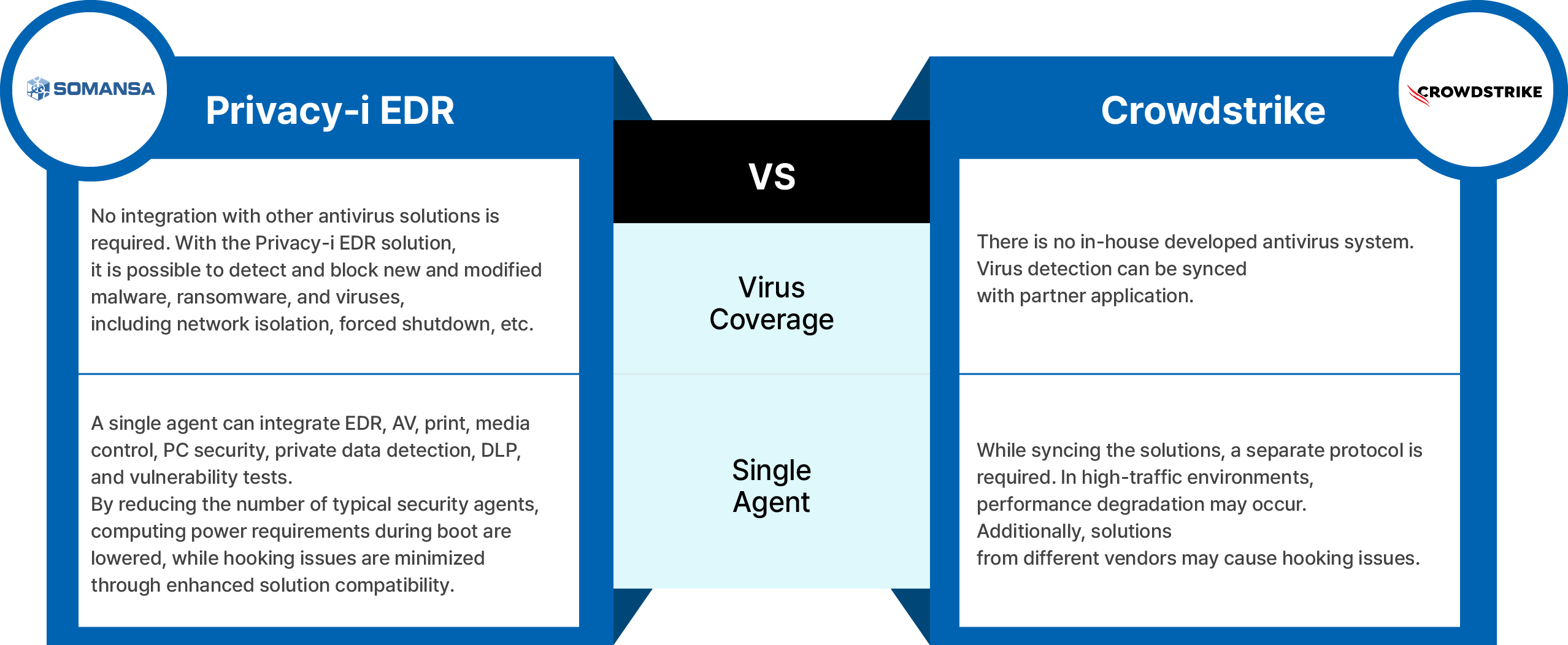
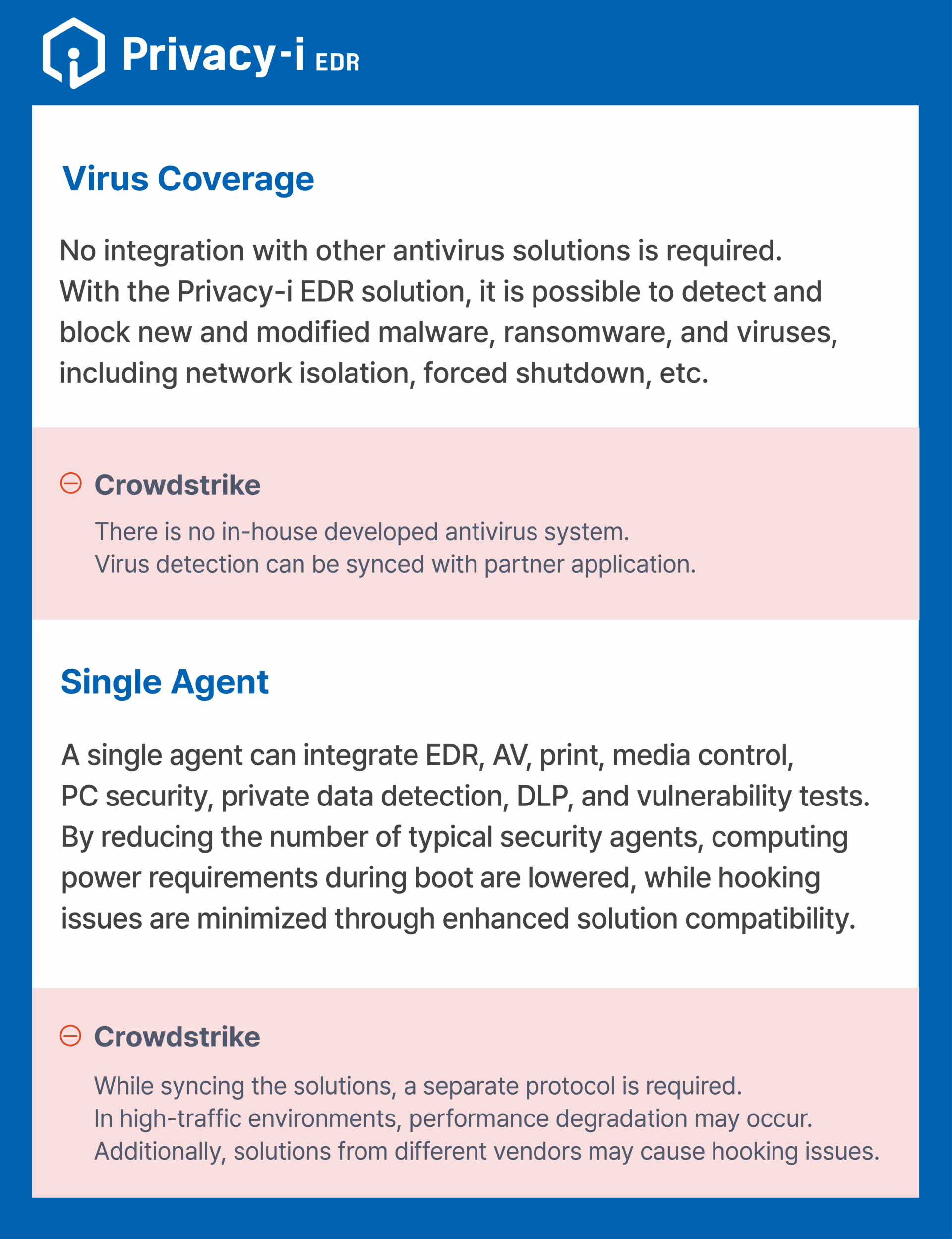
Main reference
In a 5,000-user environment, we have proven the performance and stability without any failures.